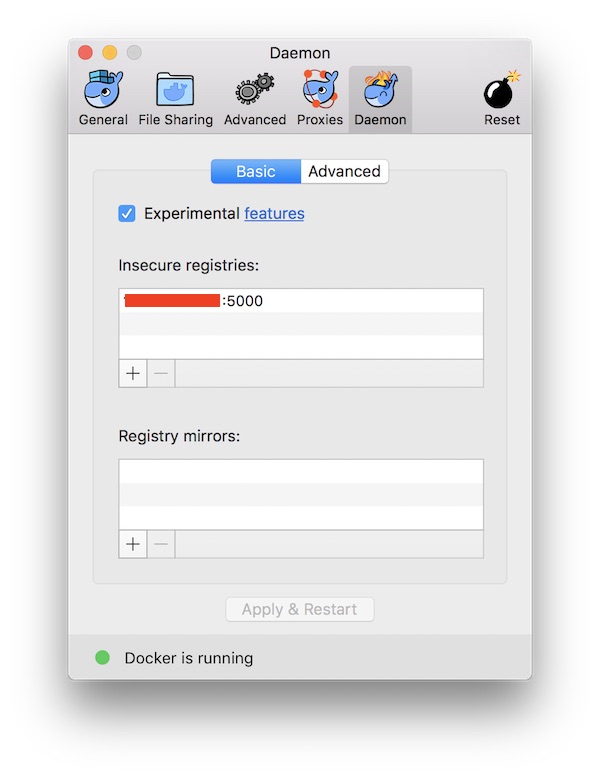
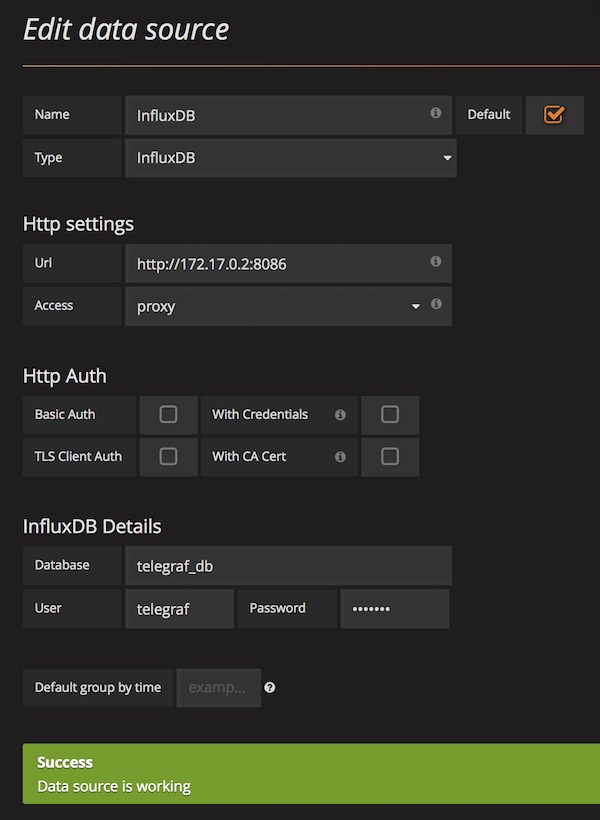
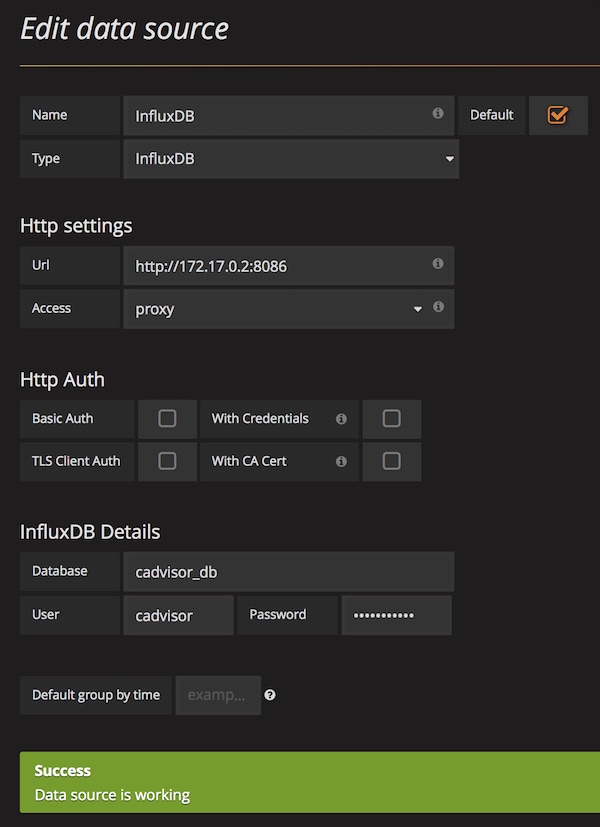
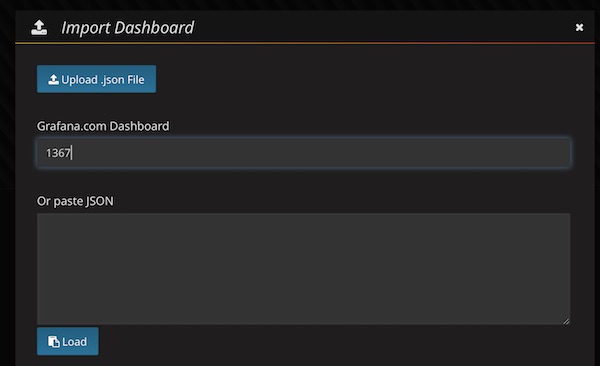
In a previous tutorial, I showed you how to set up a security learning environment quickly. Since there are some changes now (ex: Webswing), I’ll do the tutorial again. By the way i use macOS, some commands could be different but similar for Linux or Windows.
Requirements
- Docker (17.12.0-ce)
- Safari (11.02)
- Firefox (58.0)
Search and download needed docker images
# search DVWA image (optional) $ docker search dvwa # pull DVWA image $ docker pull citizenstig/dvwa # search ZAP image (optional) $ docker search zap # pull ZAP image $ docker pull owasp/zap2docker-stable # search ThreadFix image (optional) $ docker search threadfix # pull ThreadFix image $ docker pull jmbmxer/threadfix # list images (optional) $ docker images ... REPOSITORY TAG IMAGE ID CREATED SIZE owasp/zap2docker-stable latest 40848e80b7fb 2 months ago 1.33GB jmbmxer/threadfix latest b6f1907a61cd 22 months ago 941MB citizenstig/dvwa latest c8312743bc09 3 years ago 478MB ...
Run DVWA container
# run DVWA container $ docker run -d -p 8081:80 --name dvwa citizenstig/dvwa # check DVWA logs for startup (optional) $ docker logs -f dvwa # get local ip $ ipconfig getifaddr en0 ... 192.168.192.39 ... # start DVWA in browser $ open -a Safari http://192.168.192.39:8081/
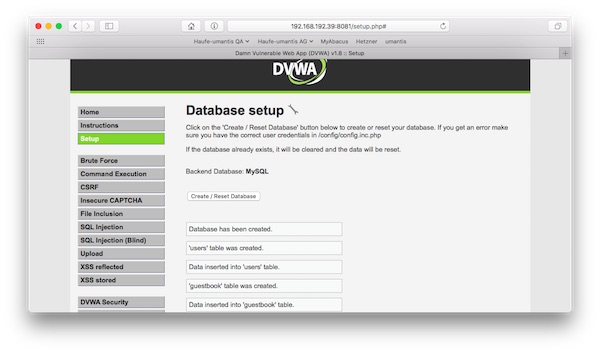
…Setup/create new database…
Run ZAP container
# create folder $ mkdir -p /tmp/reports # run ZAP container $ docker run -u zap -i -p 8080:8080 -p 8090:8090 -v /tmp/reports:/home/zap/reports --name zap owasp/zap2docker-stable zap-webswing.sh # start ZAP in Browser $ open -a Safari http://localhost:8080/?anonym=true&app=ZAP
Please check via “Tools” -> “Options” -> “Local Proxies” the right configuration!
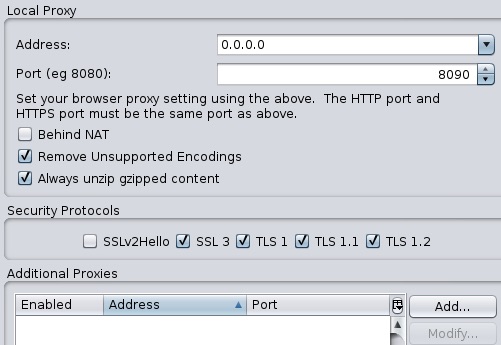
You need do use the non-routable meta address (0.0.0.0)!
Run ThreadFix container
# run ThreadFix container $ docker run -d -p 8443:8443 --name threadfix jmbmxer/threadfix start # check ThreadFix logs for startup (optional) $ docker logs -f threadfix ... Jan 30, 2018 8:56:40 AM org.apache.catalina.startup.Catalina start INFO: Server startup in 49986 ms ... # start ThreadFix in Browser $ open -a Safari https://localhost:8443/threadfix/
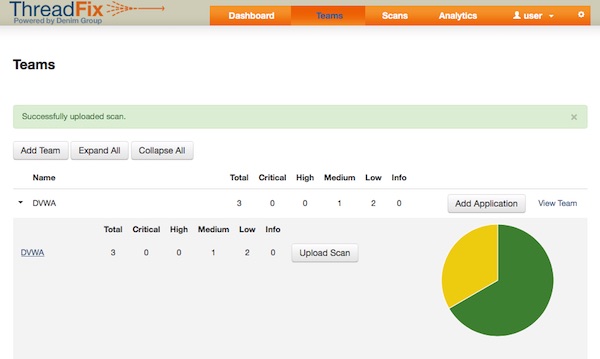
Login into ThreadFix with “user/password”

Create new team with application.
Configure Firefox
# get local ip $ ipconfig getifaddr en0 ... 192.168.192.39 ... # open Firefox preferences $ /Applications/Firefox.app/Contents/MacOS/firefox --preferences
Configure manual proxy with your local IP and 2nd ZAP port (8090). Afterwards you enable checkbox “Use this proxy server for all protocols” and press OK button.
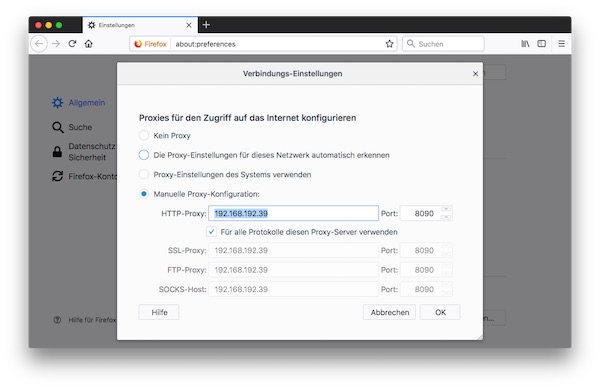
When all the configurations have been made, you can temporarily quit Firefox.
Use environment
# list all containers (optional) $ docker ps -a # open DVWA via Proxy $ open -a firefox http://192.168.192.39:8081
Start recording and save your XML report “Report -> Generate XML Report”.
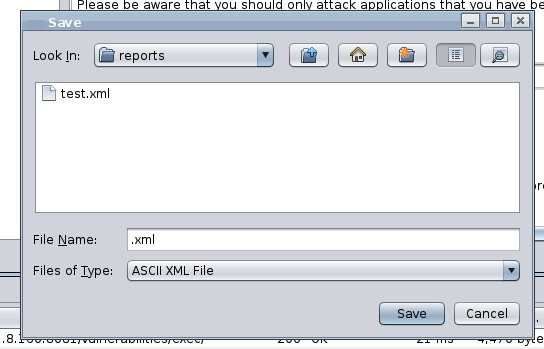
# open reports directory in finder $ open /tmp/reports
Next steps
Now it’s time to study! If you need help, you can found a lot of training materials on Youtube.