Today we build a penetration test environment via Docker. That means no Plug-Ins (for example: Java) are needed! If you are Mac OS X users, a VNC client is already included (since Yosemite).
Preparation:
# download all needed Docker images $ docker pull owasp/zap2docker-stable $ docker pull citizenstig/dvwa $ docker pull jmbmxer/threadfix # list local Docker images $ docker images ... REPOSITORY TAG IMAGE ID CREATED SIZE owasp/zap2docker-stable latest a774bdc65502 3 months ago 1.557 GB jmbmxer/threadfix latest b6f1907a61cd 5 months ago 941 MB citizenstig/dvwa latest c8312743bc09 23 months ago 478.5 MB
ZAP Attack Proxy
# run Docker container with ZAP Attack Proxy (insert and remember password) $ docker run -u zap -p 5900:5900 -p 8080:8080 -v /tmp/reports:/home/zap/reports --name zap -i owasp/zap2docker-stable x11vnc --forever --usepw --create # start VNC (Mac OS X) $ open /System/Library/CoreServices/Applications/Screen\ Sharing.app/
…or use the short way via: [cmd] + [space] and type screen sharing
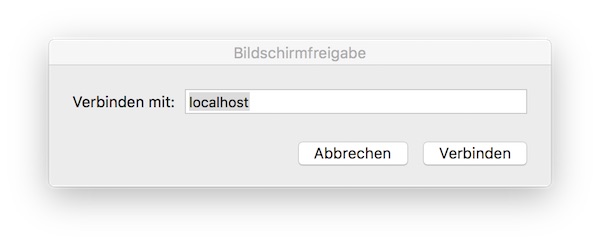
Insert “localhost” and your given password… and follow introduction for ZAP startup. Now you configure the ZAP Proxy Settings.
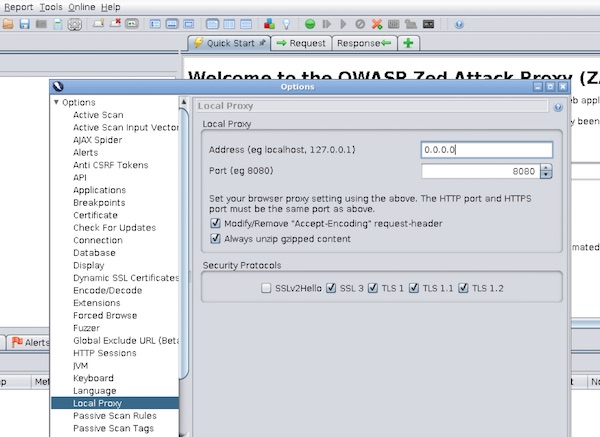
Note: Select IP “0.0.0.0” for later use. You can also use “$ docker inspect zap” to find out the internal IP, but this could change on next start.
DVWA
# run Docker container with DVWA (2nd terminal) $ docker run -d -p 8081:80 --name dvwa citizenstig/dvwa # wait for startup $ docker logs -f dvwa # get host ip (from where you run browser) $ ifconfig
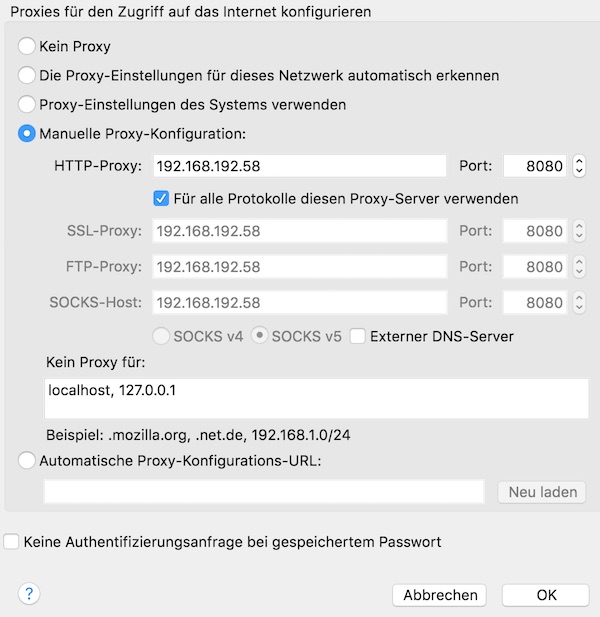
Now start your Firefox browser and change proxy settings. Insert your IP!
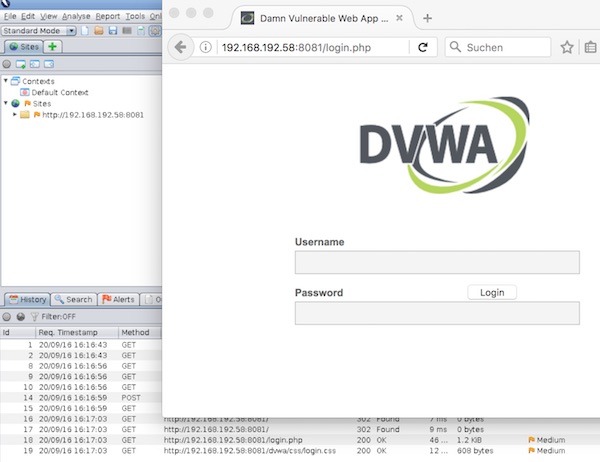
Call URL for DVWA in Firefox and run your penetration tests.
When you are done, export XML report
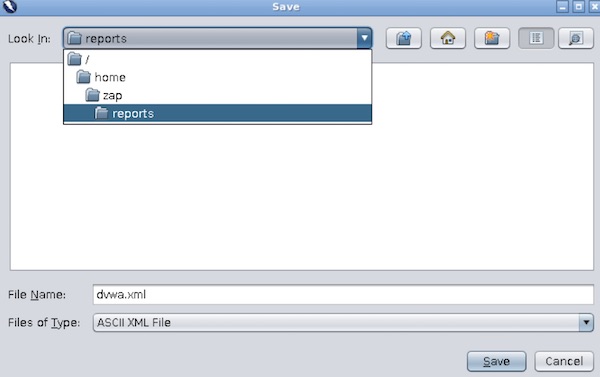
From now on, you can stop all running docker container.
ThreadFix
# run Docker container with ThreadFix $ docker run -d -p 8443:8443 --name threadfix jmbmxer/threadfix start # wait for startup $ docker logs -f threadfix
Open Safari and call URL: https://localhost:8443/threadfix. Login with User: “user” and Password: “password”. Create a new team and add a application to team.
# open directory in finder $ open /tmp/reports/
Import the ZAP XML report.
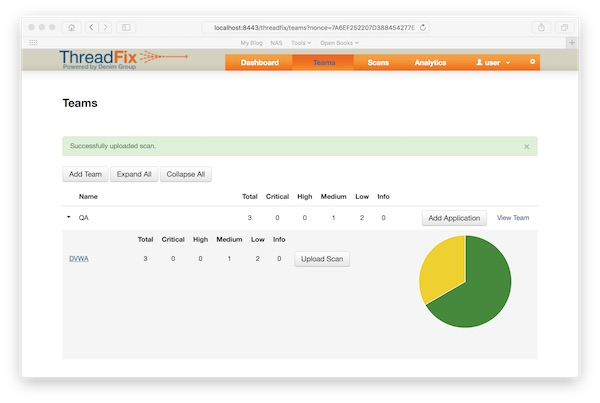
That is it… enjoy and expand your pentest laboratory!