Some time ago, I wrote a tutorial about RfCat installation on Kali Linux. Many people asked me for similar tutorial on macOS (Big Sur). So I will use this time now (my first tutorial of year 2021), to show and try to explain (as best I can do). Also I will try to provide some basics for usage, as the community seems not so big and less online documentation is available like for other topics. You can reuse the knowledge for other OS, too.
Precondition
- latest macOS Commandline Tools installed (
xcode-select --install)
Install RfCat incl. everything needed
First you need to download libusb tarball, unzip the downloaded archive and compile/install it (don’t worry sounds harder as it is). If you choose other sources like macports, you may run into location issues (paths to binaries/libraries).
Note: the following examples will just provide the latest version (1.0.24), while I was writing this tutorial. Please look beforehand if there is a newer libusb version already available.
# download via curl
$ curl -L -C - "https://github.com/libusb/libusb/releases/download/v1.0.24/libusb-1.0.24.tar.bz2" -o ~/Downloads/libusb-1.0.24.tar.bz2
# unzip archive
$ tar -xf ~/Downloads/libusb-1.0.24.tar.bz2 -C ~/Downloads/
# change into extraced archive directory
$ cd Downloads/libusb-1.0.24
# verify dependencies for build and install process are available
$ ./configure
# run build
$ make
# run installation
$ sudo make install
# verify installation (optional)
$ ls -la /usr/local/lib/libusb*
# delete archive and directory (optional)
$ rm -fr ~/Downloads/libusb-1.0.24*Install required Python packages with Python Pip. Without these the RfCat compilation, installation and usage will not correctly work!
Note: As I do have different Python version installed, I specify the excat Python version (2.7.x) in the following examples. If you have only the default MacOS Python version installed – you could use pip directly (without python2.7 -m).
# verify already installed packages (optional)
$ python2.7 -m pip freeze
# install libusb via pip
$ python2.7 -m pip install libusb
# install pyusb via pip
$ python2.7 -m pip install pyusb
# install pyreadline via pip
$ python2.7 -m pip install pyreadline
# install ipython via pip
$ python2.7 -m pip install ipython
# install PySide2 via pip
$ python2.7 -m pip install PySide2Clone RfCat Git repository from Github (may some older online documentations still link to Bitbucket). In the following example I choose the Downloads directory – of course you can choose any preferred destination.
# clone from GitHub
$ git clone https://github.com/atlas0fd00m/rfcat.git ~/Downloads/rfcat
# change directory
$ cd Downloads/rfcat
# run the installation
$ sudo python2.7 setup.py install
# verify the installation (optional)
$ ls -la /usr/local/bin/rfcat*
# show rfcat help (optional)
$ /usr/local/bin/rfcat -h
# delete cloned directory (optional)
$ rm -fr ~/Downloads/rfcatIf everything went well so far, you should take a look at your installed Python packages.
# verify installed packages (optional)
$ python2.7 -m pip freeze | grep -i 'libusb\|pyusb\|pyreadline\|ipython\|PySide2\|rfcat'Optional installation of ooktools
Now I recommend to install the ooktools packages via Python Pip. The ooktools will make your life much easier and you will have much faster results.
# install ooktools via pip
$ python2.7 -m pip install ooktools
# verify and show help (optional)
$ python2.7 -m ooktools.console --help
# verify and show specific help topic (optional)
$ python2.7 -m ooktools.console wave --helpI’ll go into the ooktools in a later tutorial, but not today.
Run RfCat
So far so good. Let’s start to connect the Yard Stick One (plug into USB) and run the first example. Always have in mind, the official operating frequencies (for the Yard Stick One):
- 300 – 348 MHz
- 391 – 464 MHz
- 782 – 928 MHz
Note: RfCat expact the values in “Hz”, so 315 MHz are 315000000 Hz.
Hint: don’t put any other transmitter next to the Yard Stick One while you use it (eq. Mobile, Wifi router, etc.). You could destroy it or weaken/disrupt your signals.
# start rfcat (interactive Python)
$ sudo rfcat -rIf no error message appears, you’re good to go.
# start scan on specific frequency (315 MHz)
In [1]: d.specan(315000000)You should see now the spectrum analyser.

Okay, stop the scanning process by closing the spectrum analyzer window. Now let’s start a simple record (also if you don’t have a signal nearby).
Note: there are many more settings and I cannot describe all here! It always depends to the problem you like/need to solve.
# enter the IDLE state (important after any action)
In [2]: d.setModeIDLE()
# specific frequency (315 MHz)
In [3]: d.setFreq(315000000)
# specific modulation (ASK/OOK/Manchester encoding)
In [4]: d.setMdmModulation(MOD_ASK_OOK)
# specific baudrate (4800 Hz)
In [5]: d.setMdmDRate(4800)
# turn on the amplifier
In [6]: d.setMaxPower()
# drops most blocks to pkts (CARRIER)
In [7]: d.lowball()
# start and dump data to screen
In [8]: d.RFlisten()
# stop listen (press Enter to stop)
# enter the IDLE state (or you need to unplug from USB)
In [9]: d.setModeIDLE()
# exit
In [10]: exit()Your result should look like:
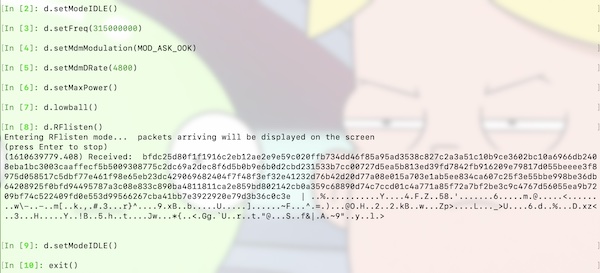
Hint: use the Tabulator key for command-line completion (also tab completion) and take use of the internal help of RfCat (eq. help(d.setMdmModulation))
The popular frequencies are mostly near by:
- 315 MHz (car fobs)
- 433 MHz (door openers, medical devices)
- 868 MHz (door openers in EU/swiss)
- 915 MHz (industrial equipment, medical devices)
Send via Python script
It would be not enough to show you only Command line and nothing about transmit. Therefore now a small Python script, which send out some example data. I think the following script is self explanatory.
from rflib import *
d = RfCat()
d.setFreq(315000000)
d.setMdmModulation(MOD_ASK_OOK)
d.setMdmDRate(4800)
print("Transmission starting")
d.RFxmit("\x2e\x2e\x2d\x2e\x2e\x2d\x2e\x00\x00\x00\x00\x00\x00"*10)
print("Transmission complete")Hint: \x escape sequence means the next two characters are interpreted as hex digits for the character code (\x is used inside strings to represent a character), 0x is used for literal numbers in Python.