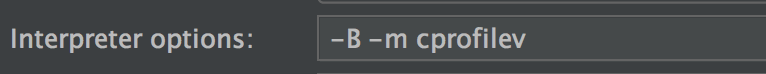
You may need to watch different log files on automated test runs. With log.io you can simply monitoring log files via browser! This tutorial shows how easy it is.
Preconditions
- Vagrant installed
Preparation
Create new project with following structure and files.
# create new project LogIO
$ mkdir -p ~/Projects/LogIO/data
# go into new Project
$ cd ~/Projects/LogIO
# create needed files in data
$ touch data/{harvester.conf,log_server.conf,web_server.conf,log.io}
# create Vagrantfile
$ touch Vagrantfile
# show files
$ tree .
.
├── Vagrantfile
└── data
├── harvester.conf
├── log.io
├── log_server.conf
└── web_server.confFile contents
# -*- mode: ruby -*-
# vi: set ft=ruby :
Vagrant.require_version ">= 1.8.1"
VAGRANTFILE_API_VERSION = "2"
Vagrant.configure(VAGRANTFILE_API_VERSION) do |config|
config.vm.box = "centos/7"
config.vm.network "public_network"
config.vm.synced_folder "./data", "/vagrant", disabled: false
config.vm.provider "virtualbox" do |vb|
vb.name = "LogIO"
vb.cpus = "2"
vb.memory = "2048"
vb.gui = false
end
config.vm.provision "shell", inline: <<-SHELL
# install needed packages
sudo yum update -y && sudo yum install -y epel-release
sudo yum install -y vim net-tools npm nodejs
sudo yum clean all
# install log.io for user <root>
sudo npm install -g log.io --user "root"
# provide custom files for user <root>
sudo rm -f /root/.log.io/*
sudo cp /vagrant/*.conf /root/.log.io/
sudo chown root:root /root/.log.io/*.conf
# provide init.d for log.io
sudo cp /vagrant/log.io /usr/local/bin/log.io
sudo chmod +x /usr/local/bin/log.io
sudo chown root:root /usr/local/bin/log.io
SHELL
end
Configure your Harvesters…
exports.config = {
nodeName: "application_server",
logStreams: {
apache: [
"/var/log/apache2/access.log",
"/var/log/apache2/error.log"
]
},
server: {
// connect to log.io server
host: '127.0.0.1',
port: 28777
}
}Configure your log server…
exports.config = {
host: '0.0.0.0',
port: 28777
}Configure your web server…
exports.config = {
host: '0.0.0.0',
port: 28778,
/*
// Enable HTTP Basic Authentication
auth: {
user: "admin",
pass: "1234"
},
*/
/*
// Enable HTTPS/SSL
ssl: {
key: '/path/to/privatekey.pem',
cert: '/path/to/certificate.pem'
},
*/
/*
// Restrict access to websocket (socket.io)
// Uses socket.io 'origins' syntax
restrictSocket: '*:*',
*/
/*
// Restrict access to http server (express)
restrictHTTP: [
"192.168.29.39",
"10.0.*"
]
*/
}
Create simple init script…
#!/bin/bash
start() {
echo "Starting log.io process..."
/usr/bin/log.io-server &
/usr/bin/log.io-harvester &
}
stop() {
echo "Stopping io-log process..."
pkill node
}
status() {
echo "Status io-log process..."
netstat -tlp | grep node
}
case "$1" in
start) start;;
stop) stop;;
status) status;;
*) echo "Usage: start|stop|status";;
esacUsage
# start VM via vagrant $ vagrant up # SSH into VM $ vagrant ssh # become root $ sudo su - # start log.io $ log.io start # get ip $ ip addr
Now open your browser with URL http://<ip>:28778