Problem
After an OS update including a restart of the system, an error occurs with SSH X11 forwarding. Instead of displaying the windows as usual, “Invalid MIT-MAGIC-COOKIE-1” is displayed in the terminal.
Here is the example. I connect to the Ubuntu with my macOS and get the error message.
┌──[lupin@HackMac]::[~]
└─ % ssh -C4Y lupin@10.0.0.12
lupin@nano4gb:~$ xeyes
Invalid MIT-MAGIC-COOKIE-1 keyError: Can't open display: localhost:10.0
lupin@nano4gb:~$ exit1st Quick and dirty solution
Since I’m on my own and relatively secure network, I leave XQuartz running in the background, disable access control, reconnect and everything works again.
┌──[lupin@HackMac]::[~]
└─ % xhost +
access control disabled, clients can connect from any host
┌──[lupin@HackMac]::[~]
└─ % ssh -C4Y lupin@10.0.0.12
lupin@nano4gb:~$ xeyes
lupin@nano4gb:~$ exitThis setting is (fortunately) only valid for this one session. As soon as I end the connection, restart XQuartz and establish a new SSH connection, the error message appears again. Anyway a not so nice solution!
2nd Quick and dirty solution
XQuartz offers the possibility to establish the connection without authentication. This solution is permanent and can be set up in the simplest way. Open the XQuartz settings and uncheck the respective checkbox.
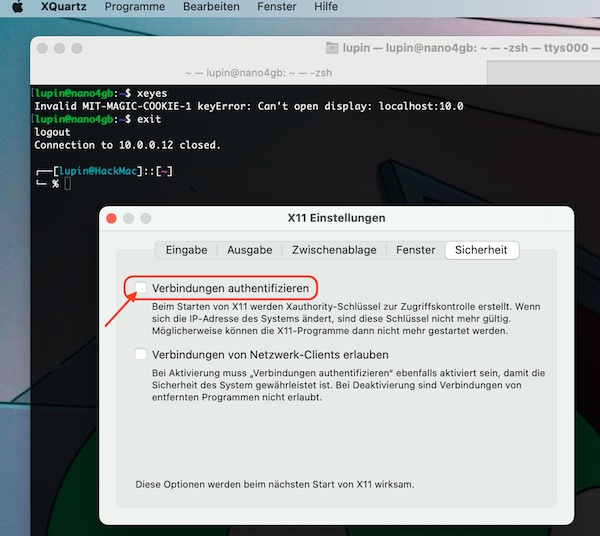
Restart XQuartz, establish a new connection.
┌──[lupin@HackMac]::[~]
└─ % xhost
access control enabled, only authorized clients can connect
┌──[lupin@HackMac]::[~]
└─ % ssh -C4Y lupin@10.0.0.12
lupin@nano4gb:~$ xeyes
lupin@nano4gb:~$ exit
Now everything works as usual. But even with this solution I have my doubts! So I undo the setting and restart XQuartz.
3rd Quick and dirty solution
As described in the previous step, I undid the setting and restarted XQuartz. Additionally I allowed local connections in the access control.
┌──[lupin@HackMac]::[~]
└─ % xhost
access control enabled, only authorized clients can connect
┌──[lupin@HackMac]::[~]
└─ % xhost +local:
non-network local connections being added to access control list
┌──[lupin@HackMac]::[~]
└─ % ssh -C4Y lupin@10.0.0.12
lupin@nano4gb:~$ xeyes
lupin@nano4gb:~$ exitThis solution also works but is not permanent and not secure.
What now?
Searching the internet didn’t really help me. Some of the suggested solutions are total nonsense (or I completely misunderstand). I’ve also read the man pages where it even says that the environment variable $DISPLAY should not be changed. With me (also due to the ignorance on my part) the first signs of despair are appearing! Trust me, I deleted also all recommended files, what did not change this situation.
My final Solution
In the end my problem was very easy to solve! I still had entries from already deleted macports in the .zprofile file, which set the local environment variable $DISPLAY. With the restart of my macOS, this export of the environment variable became active again, of course.
┌──[lupin@HackMac]::[~]
└─ % echo $DISPLAY
:0
┌──[lupin@HackMac]::[~]
└─ % vim .zprofile
# I deleted all old macports entries
┌──[lupin@HackMac]::[~]
└─ % sudo rebootThe result after the restart.
┌──[lupin@HackMac]::[~]
└─ % echo $DISPLAY
/private/tmp/com.apple.launchd.ASpxDkLA98/org.xquartz:0
┌──[lupin@HackMac]::[~]
└─ % ssh -C4Y lupin@10.0.0.12
lupin@nano4gb:~$ xeyesEverything is all right again. Oh yeah… that was troubleshooting. The good thing is I learned a lot about xhost, xauth plus my own systems.