I finally received my Yard Stick One (Yet Another Radio Dongle) and can get started with it. It is available from Hak5 (incl. ANT500 antenna) and various other resellers. In this tutorial I would like to show you, how to install RfCat on Kali Linux (version 2020.4) and point out the necessary steps, so that you can start pentesting immediately with this awesome device.
Install needed packages
The installation is actually very simple. Python3 is not a problem, even if many sources claim different. The following steps show the installation of the necessary packages (before RfCat can be installed and used). You may have already installed some of them on your system (depends on Kali Metapackages installed).
On my system following packages are installed already: curl, git, make, libusb-1.0-0, python3-numpy, python3-serial, python3-future and ipython3.
# update packages
$ sudo apt update -y
# install packages via apt
$ sudo apt install -y python3-pip python3-usb
# show python3 packages (optional)
$ pip3 freeze
# install needed python3 packages
$ sudo pip3 install PySide2 pyreadlineThe RfCat website explicitly indicates the version of SDCC (max. 3.5.0), so you can decide now to follow this request or take latest by apt.
# show package info
$ apt info sdcc
# install via apt
$ sudo apt install -y sdcc
# verify version (optional)
$ sdcc --versionIf you will not use the Kali apt repository. You can find all needed packages for “Debian stretch” here (SDCC & SDCC-Libraries).
# download sdcc-libraries package (version 3.5.0)
$ curl -l -C- http://ftp.de.debian.org/debian/pool/main/s/sdcc/sdcc-libraries_3.5.0+dfsg-2_all.deb -o sdcc-libraries_3.5.0+dfsg-2_all.deb
# download sdcc package (version 3.5.0)
$ curl -l -C- http://ftp.de.debian.org/debian/pool/main/s/sdcc/sdcc_3.5.0+dfsg-2+b1_amd64.deb -o sdcc_3.5.0+dfsg-2+b1_amd64.deb
# install sdcc-libraries
$ sudo dpkg -i sdcc-libraries_3.5.0+dfsg-2_all.deb
# install sdcc package
$ sudo dpkg -i sdcc_3.5.0+dfsg-2+b1_amd64.deb
# show version (optional)
$ sdcc --versionAlso for RfCat we don’t use the Kali apt repository but clone the GitHub repository from https://github.com/atlas0fd00m/rfcat (and install it from there).
# clone repository
$ git clone https://github.com/atlas0fd00m/rfcat.git
# change into cloned directory
$ cd rfcat/
# install rfcat
$ sudo python3 setup.py installNote: Because of security settings (of my provider), I need to show the next command as picture.
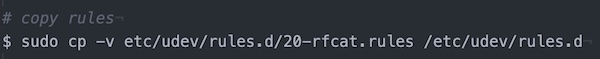
# refresh rules
$ sudo udevadm control --reload-rulesTest the installation
That was actually super easy and also happened very quickly. A little test (show help) and then you can start using Yard Stick One.
# change back to home directory
$ cd ~
# show rfcat help (optional)
$ rfcat -hIf you do not get help or an error message, please verify that all dependencies are installed or that you did not mix up different Python versions.
You may need to install the following packages: python3-pyside2.qtcore, python3-pyside2.qtgui and python3-pyside2.qtwidgets.
Run RfCat
I do run Kali Linux as VirtualBox (6.1) VM, so it’s time to plugin and passthrough the USB device.
Note: I don’t like Passwordless Sudo, but you’re welcome to customize it, to suit your needs.
# verify USB device (optional)
$ lsusb
...
Bus 002 Device 003: ID 1d50:605b OpenMoko, Inc. RfCat YARD Stick One
...
# start rfcat (interactive + d.* objects)
$ sudo rfcat -rThe following commands should help you to get familiar with the Yard Stick One device, as I want just to show the setup in this tutorial and will end here with these examples.
# show help (optional)
In [1]: help(d.setRFRegister)
# show current settings (optional)
In [2]: print(d.reprRadioConfig())
# start listen (ENTER stops)
In [3]: d.RFlisten()
# reset after scan/transmit (important)
In [4]: d.setModeIDLE()
# exit rfcat
In [5]: exit